In the dynamic era of cloud-native technologies, Kubernetes has emerged as the go-to solution for many enterprises seeking to build resilient and scalable applications. API7 Enterprise offers powerful capabilities in security and traffic management, coupled with exceptional performance. API7 Enterprise integrates with the Kubernetes Service Discovery, serving as a proxy for applications deployed within a Kubernetes cluster. Let's go exploring the process of utilizing API7 Enterprise to proxy applications in your Kubernetes cluster.
Prerequisites
- Install API7 Enterprise
Note: If API7 Enterprise is not already deployed within Kubernetes clusters, configure the network settings of the machine hosting API7 EE to ensure accessibility to upstream pods in the Kubernetes environment.
- Deploy Services in Kubernetes
If you've already deployed services in Kubernetes, you can skip this step. Otherwise, execute the following command to create services:
# create a new namespace
kubectl create namespace api7ee
kubectl create deployment httpbin --image=kennethreitz/httpbin:latest -n api7ee
kubectl create service clusterip httpbin --tcp=80:80 -n api7ee
Create a Kubernetes Service Account
API7 Enterprise relies on this credential for accessing the Kubernetes API and fetching upstream configurations. Consequently, We need to create an
RBACresource first. The following is the specificYAMLfile configuration:# rbac.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: api7-k8s-sd-watcher rules: - apiGroups: [""] resources: ["endpoints"] verbs: ["list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: api7-k8s-sd-watcher-binding subjects: - kind: ServiceAccount name: api7-k8s-sd-sa namespace: api7ee roleRef: kind: ClusterRole name: api7-k8s-sd-watcher apiGroup: rbac.authorization.k8s.io --- apiVersion: v1 kind: ServiceAccount metadata: name: api7-k8s-sd-sa namespace: api7ee --- apiVersion: v1 kind: Secret metadata: name: api7-k8s-sd-secret namespace: api7ee annotations: kubernetes.io/service-account.name: api7-k8s-sd-sa type: kubernetes.io/service-account-tokenCreate RBAC resources and get this token.
kubectl apply -f rbac.yaml -n api7ee kubectl get secrets api7-k8s-sd-secret -n api7ee -ojsonpath='{.data.token}' | base64 -d
Implementation of Kubernetes Service Discovery in API7 Enterprise
Connecting to the Kubernetes Service Registry
Go to an existing gateway group and access the Service Registry through the left-hand menu.
Click the Add Service Registry Connection button. Select Kubernetes as the discovery type and provide the Kubernetes API service access address and token.
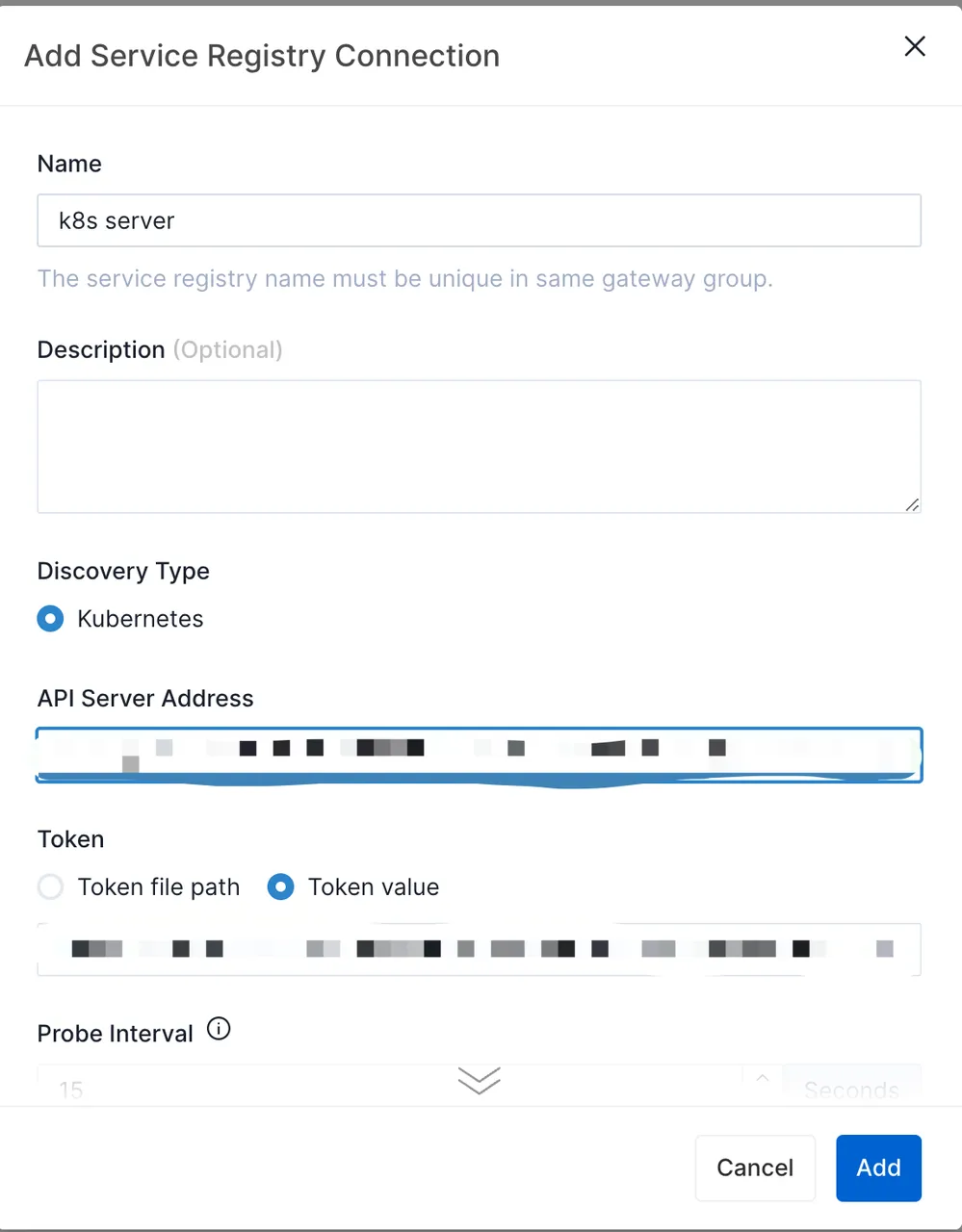
- Once API7 Enterprise establishes a successful connection to the service registry, you will see a healthy status.
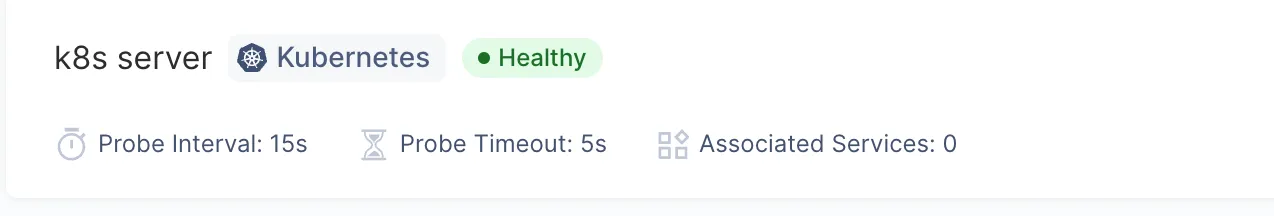
Publishing the Service for Testing
Navigate to the service page, click to create a new service, and add the
/anythingroute.Proceed to publish the service, and choose the appropriate upstream:
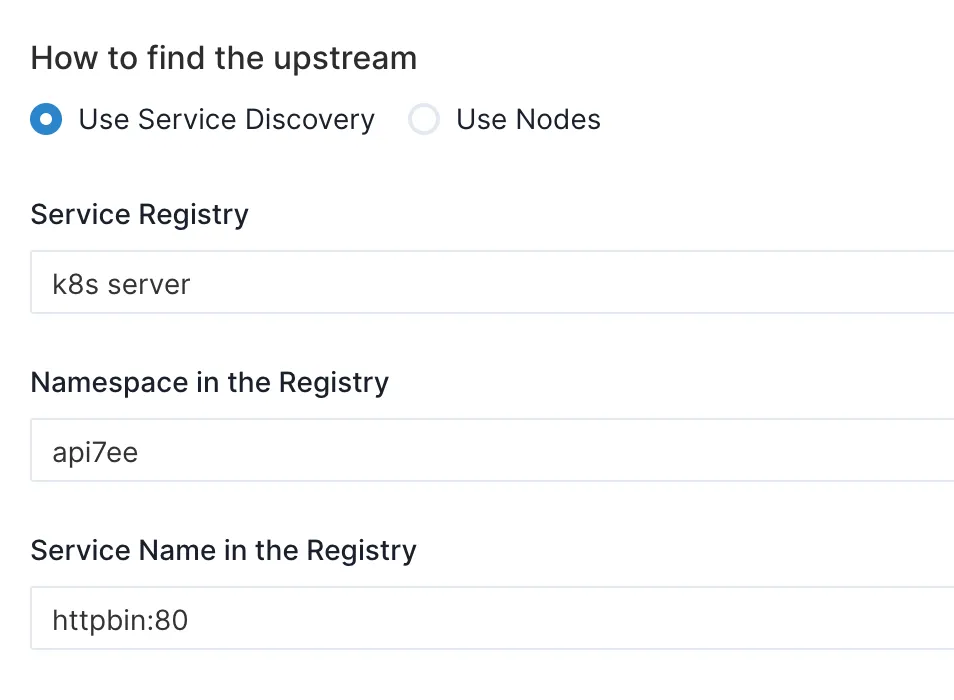
- After publishing, you can test it using
curl.
Summary
In conclusion, we have talked about the steps to leverage the API7 Enterprise for proxying Kubernetes services. For more information about the features of the API7 Enterprise, please don't hesitate to get in touch with us.
